With industry 4.0 come inherent security risks.
New and emerging risks are arising as the industrial landscape is becoming increasingly connected. With newer devices and technologies emerging, IoT is getting more closely integrated with everyday businesses, subsequently expanding. These devices have become part of our everyday life and play a vital role in various industries, including IoT. As of this, Cyber security strategies encompassing all the technologies and operations should be implemented to safeguard platforms and networks from cyber-attacks.
Our Layered Cyber Security approach for IoT Industry
Different industries use a variety of security practices and standards to ensure security solutions. It is crucial to adopt a security strategy that can cater to the needs of Industry 4.0 at scale. Using 3rd Generation Partnership Project(3GPP) standards, we connect smart devices and systems instead of relying on the fragmented landscape of industry best practices, as it is the best way forward to secure industry 4.0 IoT networks.
Secure Products
In an interconnected world, high levels of protection of devices, data, interfaces, and network elements are essential. For all networks, it is crucial to consider perimeter protections using gateways or firewalls, traffic domain separation, and control to prevent potential threats and minimize the risk of attacks.
Selecting products that are easy to integrate, pose no risk to data privacy and security, and are ready to withstand potential threats is a must. Security must be built in from the start of the product development, not as an afterthought. Besides securing the products, it is crucial to ensure security and identity functions across all domains.
Security Operations
The IoT implementation technique of businesses plays a vital role in securing devices and systems. The more connected the production network becomes, the more critical it becomes to separate it from the IT network. Organizations should make sure of physical security during risk assessment. All industries, inclusive of IoT, need an end-to-end security management system that provides:
- Automation of security policy for compliance to industry standards and objectives.
- Timely detection and response to security threats by evaluating security analytics.
- Risk intelligence for a continuous string security posture.
Security Management
End-to-end security is a must-have to keep IoT networks safe and secure, from connected devices to access and network through to cloud and apps. Intrusion Detection and Prevention System (IDPS) and Security Incident and Event Management (SIEM) systems are core parts of incorporation in security management strategy.
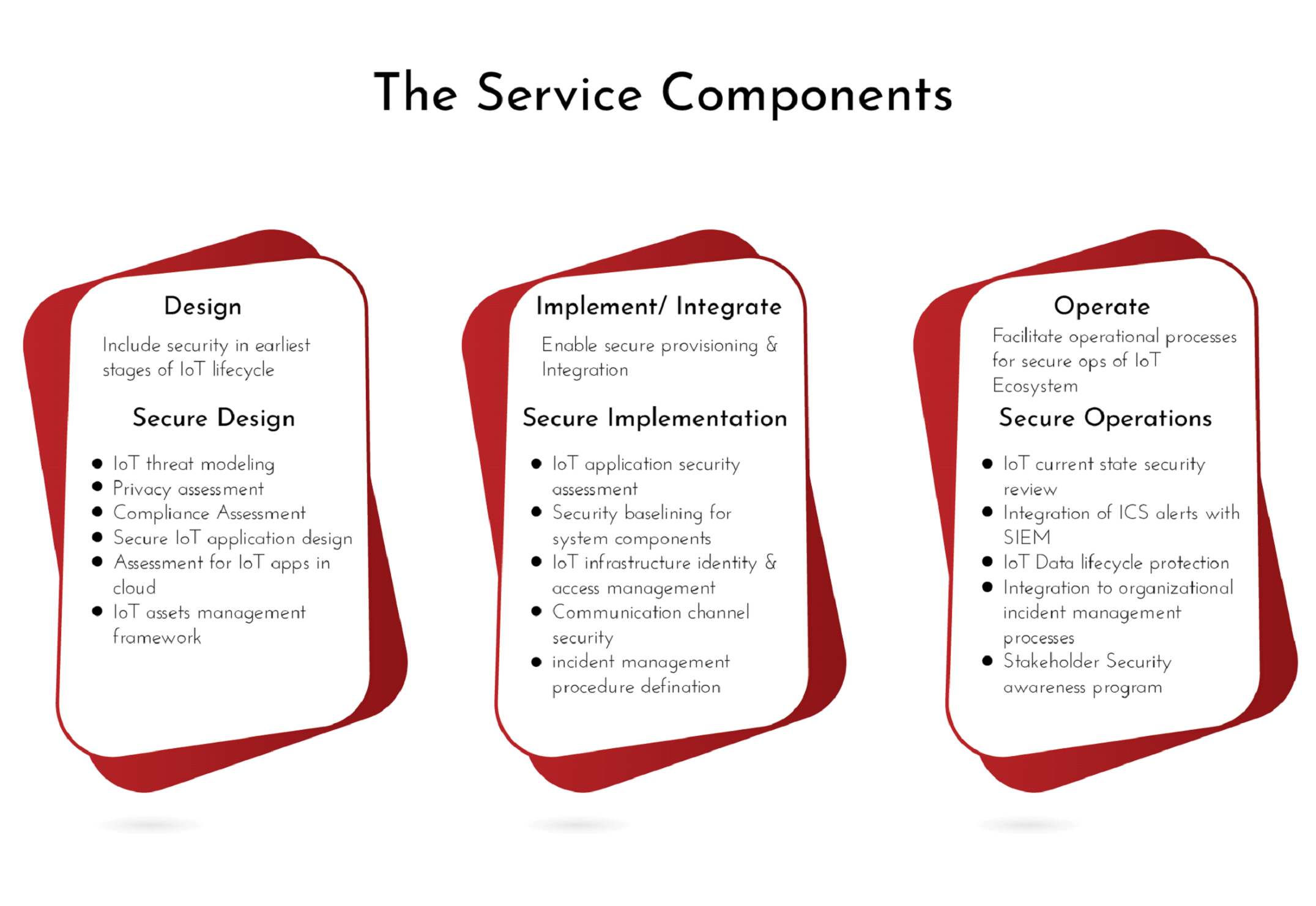
Our Cyber IoT Services
IoT Security Program Design, Development, Implementation, and Operation
We design, develop and implement a security pathway that enables organizations to manage cyber risks associated with IoT networks.
Security Testing
We do technical security testing, including the latest techniques and procedures that utilize manual and automated tools and reviews to detect potential threats at the hardware, software, and firmware level. It also includes testing of management, monitoring, and logging.
Security Engineering
Our cyber experts’ design, develop, and implement the IoT products for security implementation and their associated ecosystem.
Supportive Technology and Tooling
We offer an end-to-end centralized tool that assists in the management and operations of IoT security programs, including risk management and associated processes.
Risk Assessment
To assess risk, we do paper-based security testing based on stakeholder feedback to help identify potential vulnerabilities at the device level and drive remediation activities.
Security Advisory
We advise organizations on a situational response like crises management, transactions, and regulatory inquiry.
Asset Management, Monitoring, and Response
Likewise, we evaluate products using third-party technologies which proactively identify and remediate risks as they occur.
Conclusion
Modern IoT ecosystems are complex. The digital risk is present at every step along the IoT journey. For us at Zigron, the first step for any IoT business is to undergo a thorough security risk assessment that examines vulnerabilities in devices and network systems with the help of our Cyber Security experts. Risk must be mitigated for the entire IoT lifecycle, especially as it scales and expands geographically.
While businesses, government, and health care sectors have increasingly benefitted from IoT, the interconnectedness of devices has raised the stakes in terms of risk and potential security damages that can occur. In light of challenges posed by IoT Security complexity, we help perceive cost implementation that aims to highlight strategies to become successful and cost-effective while employing IoT Security.
